Privileged account management (PAM) has emerged to be one of the hottest topics of the cybersecurity industry, all because of the everlasting impacts that a simple mistake could lead to. Cybercriminals are always on their toes when it comes to intercepting the connections, stealing the target’s privileged credentials, and compromising the data. The situation is all the more severe as, when an attacker gets his hands on these credentials, he poses himself as a trusted user and enjoys unfettered access to the critical assets of an organization for months without getting detected.
Things can turn out to be uglier with insider threats. More often than not, insider attacks are caused by honest mistakes, like opening phishing emails and clicking on dubious links.
It is worth mentioning here that employees are not the only ones with insider access. If you outsource your IT operations or use third-party tools, or have certain consultants and vendors connected to your network, the chances of such attacks become even higher, and it gets all the more difficult to maintain security in such cases.
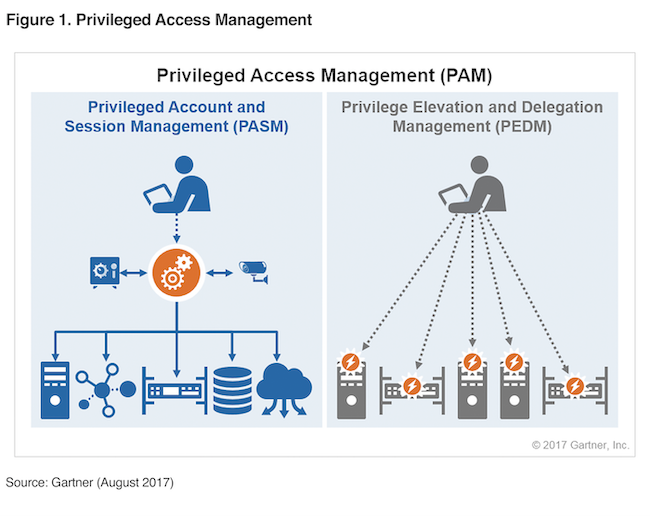
What is PAM ?
PAM, or privileged access management, is a solution that helps organizations manage the privileged access to prevent unauthorized access to the crucial data and reduce the risks.
Why is PAM A Must for Every Organization ?
According to an estimate, the global average cost of data breaches amounts to around $3.62 million. This is enough to inspire the CISOs (chief information security officers) to take steps in the right direction to manage the privileged accounts comprehensively and robustly.
It is surprising to know that even after realizing the importance of privileged account management, organizations are not at all serious about it, and 54% of companies still use Excel or paper to manage privileged credentials.
Partly, this is because most vendors do not offer a complete solution, but rather provide point solutions, such as session recorders and password managers, that only meet the half the requirements. But this doesn’t mean that robust PAM solutions do not exist in the market. They do, but often they are hard to deploy and are difficult to integrate with business-critical technologies.

It is the need of the hour that businesses stop keeping their data at stake and move beyond spreadsheets to mitigate risks and get a better ROI.
There are various high-end PAM solutions available in the market which are easy to deploy and integrate with existing technologies and provide a more comprehensive set of functionalities.
Overall, the latest PAM tools available in the market help in :
● Establishing well-defined custom flows for gaining privileged access.
● Recording and monitoring activities on privileged accounts to aid forensics and audits.
● Discovering all privileged users and accounts across the organization.
● Automatically prompting the users to change their passwords, and changing them automatically when employees leave the company.
Do Not Confuse PAM with IdM
More often than not, PAM is confused with IdM, which is the broader category of privileged access management. While PAM is focused more on the access of the privileged user, IdM is all about authenticating and authorizing the user to make sure that the right person is logging in.
Best Privileged Access Management Softwares
With this in mind, let’s have a look at some of the best PAM software (according to Gartner) that we have with us today :
Thycotic
Thycotic secures your apps and streamlines your business operations. The software comes along with a range of features such as single sign-on, multi-factor authentication, mobility management, and others.
The software verifies every user, validates their devices, and provides them with the required access and privilege accordingly.
Probably one of the best parts of Thycotic is that they can take care of your problems with your existing solutions and propose a viable solution that is in line with your business.
Applications : It is suitable for a range of industries including service industry, education industry, and transportation industry, manufacturing industry, retail industry and others.
Pros :
- Simple implementation
- Easy to use interface
- Provides good customer support
- Reliable with consistent results
Cons : Interface is limited in terms of customization

CyberArk
CyberArk provides enterprises with robust security and managed users and groups. The software helps you in meeting your compliance requirements and reducing security risks.
Further, the company is quite proactive in terms of communication and is willing to support.
However, one downside associated with CyberArk is the steep learning curve. The backend is a bit difficult to understand, and documentation does not help a great deal.
Applications : The software would work fine for finance, media, government, healthcare, retail and education industry.
Pros :
- Responsive and quick support
- Easy to deploy
- Easy to integrate with standards APIs and tools
Cons : High-end configuration is difficult
BeyondTrust
BeyondTrust PAM is one of the best in the market. The vulnerability management and privileged account management solutions provided by the company reduce the risk of data thefts and positions you to better act against data breaches.
Applications : The product is versatile and fits a range of industries including finance, manufacturing and others pretty well.
Pros :
- Easy to customize and enhance
- Manages passwords effectively
- Migration is easy
- Updates are rolled-out frequently
Cons :
- Documentation needs improvements
- A bit of learning curve is involved
- Implementation could be a bit tough
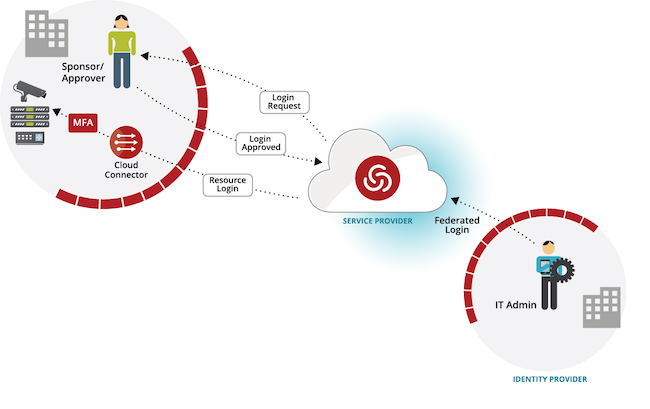
Centrify
Centrify is a renowned name in the field of security and uses next-gen technology to stop data breaches. The PAM software works by strengthening your security and making it easier to authenticate users.
Applications : The software is easy to implement and fits in a range of industries including retail, services, IT, manufacturing and others.
Pros :
- Offers easy to manage enterprise password management services
- Can be set up in cloud or on-premise
- Quick support
Cons :
- Implementation is a bit tough
- Documentation involves a steep learning curve
The entire process of defending your business processes from the mismanagement of privileged accounts can seem to be daunting at first but plays a crucial role. The conventional security tools would not raise the alarm when someone is using legitimate authentication for mysterious purposes.
As they say, the more people have access to your data, the more are the chances of a data breach. Thus, it is necessary that you keep a check on all your privileged accounts and have a proper privilege account management software in place.
Sources :
https://www.gartner.com/reviews/market/privileged-access-management-solutions/vendor/cyberark
https://www.gartner.com/reviews/market/privileged-access-management-solutions/vendor/centrify
https://www.gartner.com/reviews/market/privileged-access-management-solutions/vendor/BeyondTrust
https://www.gartner.com/reviews/market/privileged-access-management-solutions/vendor/Thycotic
http://blog.wallix.com/what-is-privileged-access-management-pam